SKUDONET is a forward-thinking leader in the Application Delivery Controller sector, dedicated to ensuring secure and efficient delivery processes. In recognition of the contemporary business landscape, it’s evident that security looms as a paramount concern. Addressing this, we recognize the potential in incorporating this task into the administration of the controlling application. This strategic integration ensures that exclusively benign traffic permeates our backend infrastructure.
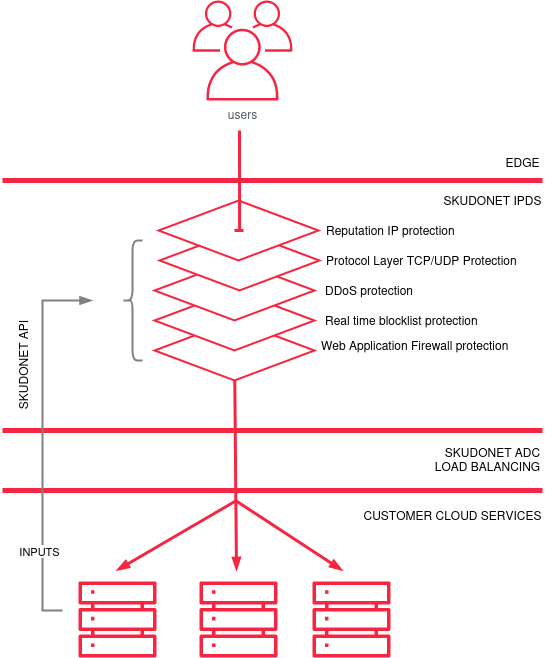
Given the present demand for a robust online defence strategy, the engineers at SKUDONET have conceived a groundbreaking security and detection mechanism that aims to counteract an array of threats. Named the Intrusion Prevention and Detection System (IPDS), it abides by the following principles:
The Edge Takes Center Stage: Edge computing, a modern paradigm, situates computational power proximate to the final service destination. This configuration optimizes latency and allocates dedicated tasks to alleviate the end-resource burden. Thus, the edge’s potential extends to encompass protective measures, sieving out malicious traffic. Clean, legitimate traffic alone proceeds to customer services.
Strategic Defense Yields Resource Conservation: With the edge’s establishment as a custodian of customer services, optimizing computational efficiency is pivotal. Once an unauthorized packet is detected by the SKUDONET IPDS module – stationed at the edge – substantial resource savings are realized. This proactive approach enables SKUDONET IPDS to shield the system during ingress, entrenched within the SKUDONET Operating System. Scaling linearly through the addition of CPU cores, it boasts the capacity to stave off over 45 million packets per second per core.
Diverse Threats, Diverse Defenses: A singular cybersecurity remedy is a mirage, incapable of thwarting all assaults. However, a multi-layered solution fortifies a system against well-known exploits and zero-day attacks. The aspiration is to scrutinize traffic for discernible attack patterns or suspect origins. This multi-tiered security model is the bedrock of our solution.
Let’s delve deeper into the modus operandi of an efficacious multi-layered security framework at the Edge.
Client Standing.
At the Edge, the client’s IP undergoes scrutiny, preemptively barring access from malevolent sources. IPs marked as assailants through third-party reports signify their notoriety. Leveraging this intelligence, SKUDONET thwarts potential threats. Pre-built reputation sets, tailored to countries or IP addresses implicated in attacks on services like SMTP, IMAP, Databases, PBX or SIP Servers, Web or API services, public Proxies, TOR networks, and Bot networks, contribute to server protection. SKUDONET IPDS encompasses over 250 IP client reputation databases, updated daily, while bespoke sets are also feasible.
Denial of Service (DoS) Safeguard
The Edge evaluates packet behavior to mitigate various DoS attacks. Deploying diverse packet inspection rules prevents attempts to overwhelm client-facing services. Defense mechanisms target high request rates per second per source IP or destination IP, reset packet flooding, bogus attacks, and others.
Real-time Blocklist (RBL) Defense
At the Edge, SKUDONET wields real-time blocklists, fending off diverse sources through source IP DNS Resolution. This versatile solution harmonizes any flow with one real-time blocklist system, extending beyond SMTP traffic. Leverage a shared database for several application services, choosing between our exclusive RBL system or renowned third-party services like Spamhaus, Spamcop, and other public alternatives.
Reimagining Reverse Proxy
Upon SKUDONET IPDS capturing an HTTP flow, its trajectory shifts through an Edge-located reverse proxy, presiding before your web backend server. The security dividends conferred by SKUDONET IPDS upon your service are delineated below:
Transport Layer
In its capacity as an Edge device, SKUDONET IPDS secures the TCP layer repelling SYN flood attacks by using SYN proxy. This feature fabricates two independent connections: a TCP link connecting the client and SKUDONET IPDS at the Edge, and another binding SKUDONET to backend servers, inoculating against TCP-based assaults.
Application Layer
At the Edge, SKUDONET IPDS selectively opens used ports (most commonly 80 and 443 for Reverse Proxy applications), only allowing traffic through them, and, therefore, defending against port scanning or improving scoring in any Cybersecurity Audits. Within the reverse proxy layer, the IPDS module exclusively accommodates HTTP(S) protocol, warding off malformed solicitations. It tactically awaits the reception of complete HTTP headers from clients before analysis and onward transmission to servers. This sequential analysis averts Slowloris attacks, while a Web Application Firewall feature further inspects web content.
WAF: Web Application Firewall
The surge in HTTP(S) traffic compels a robust security layer. An excellent example of the need for security is the case of Exchange Server which in the later version is managing its services through HTTP(S) protocols. For this reason, HTTP(S) protocol inspections and analysis in the Edge are combined with the SKUDONET IPDS security layer fortified with prebuilt rules (OWASP) or custom-made rules, continuously being updated to counter emerging threats. These encompass diverse vulnerabilities – HTTP(S) methods enforcement, DoS, Scanner detection, protocol enforcement, protocol attack, LFI/RFI/RCE attacks, XSS or Cross-site scripting, SQLi or SQL Injection, Application session-fixation attack, and security of web projects spanning WordPress, Drupal, NextCloud, Dokuwiki, Cpanel, Xenforo, and more.
IPDS: Safeguarding through Multiple Layers
At its core, the SKUDONET IPDS module forms an initial bastion against attackers, sieving out nefarious traffic. This ensures the passage of only legitimate communication through your cloud-bound system or servers, exclusively permitting connections from SKUDONET IP services. Beyond this, SKUDONET IPDS extends a REST API for remote rule updates, accommodating external devices like backend servers. This external engagement facilitates rule updates, especially in instances where mitigation requires remote intervention, effectively bridging the gap to cloud customer service.
Concluding Remarks
Initiating at the Edge, SKUDONET IPDS lays the cornerstone for service security. Our exposition detailed the efficacy of SKUDONET IPDS in fostering a resilient multi-layered solution. With over 5000 dynamic protection rulesets, daily updates ensure your system’s readiness against evolving attackers and methods jeopardizing your cloud-based services. Should you seek an expanded understanding of SKUDONET IPDS’ potential to bolster your infrastructure, we encourage you to contact us. Collaboratively, we can forge a security platform tailored to your specific exigencies.