Contents
Role-Based Access Control
SKUDONET Load Balancer includes a Role-Based Access Control (RBAC) module. RBAC is a policy-neutral access control mechanism that uses users, roles, and privileges to define who has access to what. The RBAC module connects to different data sources to authenticate users.
Supported Data Sources
The RBAC module supports two data sources:
- LDAP: The users are authenticated against an existing LDAP system, such as OpenLDAP or Microsoft Active Directory.
- Local: The users are authenticated against the Local Linux user database. If the cluster is running the users are synchronized between both nodes ( from MASTER to BACKUP).
Validation System Configuration
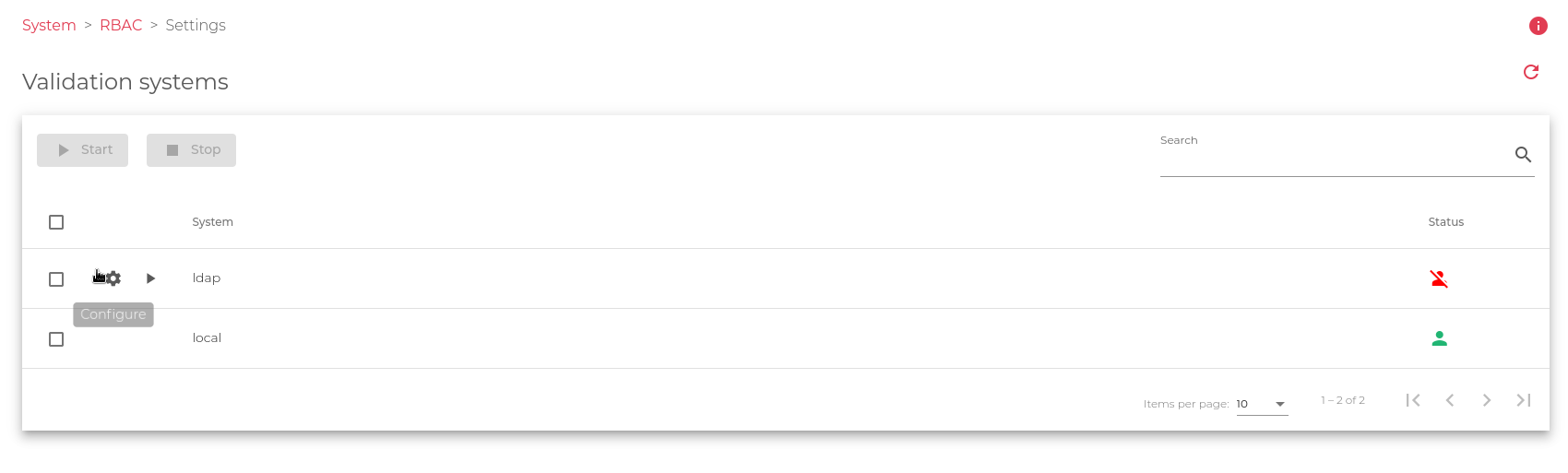
As shown in the screenshot, the validation systems can be enabled or disabled as needed. If multiple validation systems are enabled, the system will first try to authenticate the user against the LDAP system. If the user is not found in the LDAP system, the system will then try to authenticate the user against the local Linux user database.
Validation System Fields
The following fields are available in the Validation System table:
System: Defines the validation module for logged-in users. In this version, logins against LDAP and Local are supported. In the case of LDAP validation, the system must be configured as described in the later chapters of this section.
Status: The status of the validation system.
 Enabled: The green icon indicates that the validation system is active
Enabled: The green icon indicates that the validation system is active Disabled: The red icon indicates that the validation system is disabled.
Disabled: The red icon indicates that the validation system is disabled.
Actions: The supported actions for the validation system are:
- Start: Activates the usage of the authentication module.
- Stop: Deactivates the usage of the authentication module.
- Configure: Set up the validation module and run some tests to check if the LDAP connector is properly configured.
LDAP Validation Connector Configuration
To configure the LDAP validation connector, you must provide the following information:
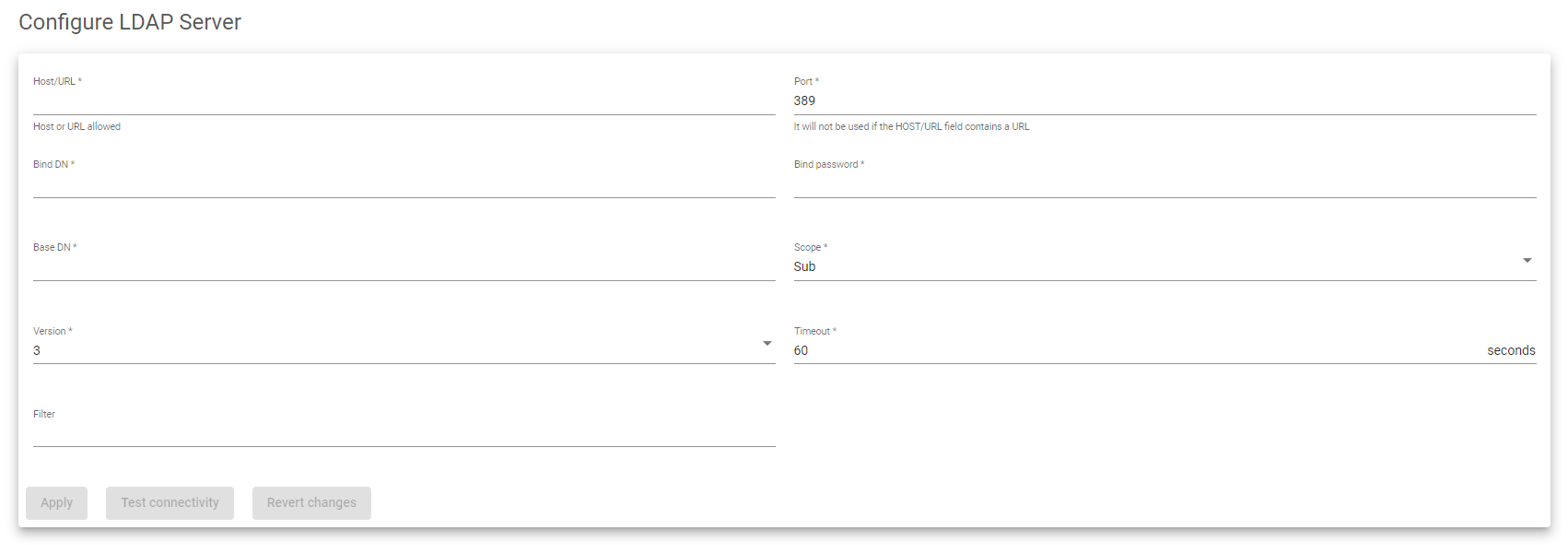
- Host/URL: The address of the LDAP server.
- Port: The TCP port on which the LDAP server is listening. By default, this is 389 for LDAP or 636 for LDAPS (SSL).
- Bind DN: The username and password used to authenticate to the LDAP server.
- Base DN: The starting point in the directory where the LDAP server will search for users to authenticate.
- Scope: The depth of the LDAP search.
- Version: The version of the LDAP protocol that will be used to communicate with the LDAP server.
- Timeout: The amount of time to wait for the LDAP server to respond to a search request before timing out.
- Filter: An expression that specifies or limits the number of users or groups that can access an application.
The following search is an example that uses the fields described above. It shows that a user can be found in the LDAP directory in addition to the Bind DN user.
root@client:~$ ldapsearch -h ldap.skudonet.com -D cn=admin,dc=skudonet,dc=com -b ou=people,dc=skudonet,dc=com -W Enter LDAP Password: # extended LDIF # # LDAPv3 # base <ou=people,dc=skudonet,dc=com> with scope subtree # filter: (objectclass=*) # requesting: ALL # # people, skudonet.com dn: ou=people,dc=skudonet,dc=com objectClass: organizationalUnit objectClass: top ou: people # acano, people, skudonet.com dn: cn=acano,ou=people,dc=skudonet,dc=com cn: acano givenName: alvaro gidNumber: 500 homeDirectory: /home/users/acano sn: cano loginShell: /bin/sh objectClass: inetOrgPerson objectClass: posixAccount objectClass: top uidNumber: 1000 uid: acano userPassword:: e2NSWVBUfXVLdFcxNGZaOGfdaJyZW8= # search result search: 2 result: 0 Success # numResponses: 3 # numEntries: 2
The UID and password attributes are used to authenticate users to the RBAC module.
Once you have confirmed that the required attributes are correct and that the LDAP search is working, you can configure the RBAC LDAP module as follows:
LDAP Server: ldap.skudonet.com Port: 389 (default) Bind DN: cn=admin,dc=skudonet,dc=com Bind DN Password: Secret password Base Search: ou=people,dc=skudonet,dc=com Filter: Not used in this example
Note that the Filter field is optional. If you do not specify a filter, all users in the LDAP directory will be able to authenticate to the RBAC module.
Considerations
Host field: The Host field can be either an IP address or a URL. If you want to specify the protocol (LDAP or LDAPS), use a URL (e.g., ldap://ldap.skudonet.com or ldaps://ldap.skudonet.com).
Port field: You do not need to specify the port field if you configured a URL in the Host field. The port is implied by the protocol (LDAP or LDAPS). However, if the LDAP port you are using is not the default, you must specify the port.
Scope field: The Scope field controls the depth of the LDAP search. There are three possible values for the Scope field:
- Sub: The search is performed in the configured Base DN and all of its sub-levels.
- One: The search is performed in the configured Base DN and one level below.
- Base: The search is only performed in the configured Base DN.
Filter field: The Filter field is used to specify a condition that must be met for a login to be successful. For example, if the UID attribute does not contain the value specified in the Filter field, the login will fail even if the password is correct. The Filter field can also be used to modify the login behaviour if the LDAP system uses a different attribute for login purposes. For example, Active Directory uses the sAMAccountName attribute for login. You can concatenate filters together to create complex conditions. For example, the following filter would only allow users who are members of the sysadmins group to log in:
(&(sAMAccountName=%s)(memberOf=CN=sysadmins,OU=yourOU,DC=yourcompany,DC=com))
Next Article: System | RBAC | Users

