Contents
A brief intro to SKUDONET CE v7.2.0
The new improvement that the SKUDONET Development team has included in SKUDONET Application Delivery Controller Community Edition is the Web Application Firewall Module, this new module offers cyber security capabilities for HTTP and HTTPS farms and makes SKUDONET the first Open Source Load Balancer that includes Web Application Firewall features.
SKUDONET Open Source Load Balancer v7.2.0 is now an Open source Web Application Firewall that uses ModSecurity v3.0.13 library, this library permits to use of a declarative language to analyze the HTTP/S traffic and interact with him.
In this article, we will describe how to load OWASP rulesets compatible with SKUDONET v7.2 and how to protect a Load Balanced farm with those security rules.
Update from SKUDONET v7 to SKUDONET v7.2 Open Source Community Edition.
Ensure the Debian APT repositories for SKUDONET v7 are configured:
root@skudonetlb#> cat /etc/apt/sources.list deb http://deb.debian.org/debian/ bookworm main non-free-firmware deb http://deb.debian.org/debian-security/ bookworm-security main non-free-firmware
And the SKUDONET APT Community repositories are configured as well:
root@skudonetlb#>cat /etc/apt/sources.list.d/skudonet.list deb http://repo.skudonet.com/ce/v7/ bookworm main
Now proceed to update the packages
root@skudonetlb#> apt-get update root@skudonetlb#> apt-get install skudonet skudonet-gui-core
Open a new browser and check the new aspect. Now, a new option in the lateral menu is shown: “IPDS” (Intrusion Prevention and Detection System) with a WAF submenu.
This new section of WAF allows you to create Seclang rules using a semantic analyzer that highlights the code to let you manage this declarative language. Additionally, this new module highlights Lua Language, which is used by SKUDONET WAF to extend functionalities.
Install the OWASP CoreRuleSet Rules in the SKUDONET Community version
Go to a directory to download the OWASP CoreRuleSet
root@skudonetlb#> cd /opt
Download the latest OWASP CoreRuleSet
root@skudonetlb#> wget https://github.com/coreruleset/coreruleset/archive/refs/heads/main.zip
Decompress the OWASP CoreRuleSet file
root@skudonetlb#> unzip main.zip
Copy all the Rulesets and data to the SKUDONET IPDS WAF Rulesets config directory
root@skudonetlb#> cp coreruleset-main/rules/* /usr/local/skudonet/config/ipds/waf/sets/
Copy the setup example file to the SKUDONET IPDS WAF Rulesets config directory It is mandatory to setup tx.crs_setup_version
root@skudonetlb#> grep -v "^SecDefaultAction" coreruleset-main/crs-setup.conf.example > /usr/local/skudonet/config/ipds/waf/sets/REQUEST-90-CONFIGURATION.conf
The SKUDONET Opensource Load Balancer has all the OWASP Rulesets and can be applied to the HTTP/S Farms.
Now all the content in the indicated directory /usr/local/skudonet/config/ipds/waf/sets/ can be shown from the web GUI section “IPDS > WAF ”
Enable SKUDONET Open source WAF for a SKUDONET Farm.
Now that SKUDONET Open Source WAF is loaded with SecLang rulesets you can add those rulesets to the HTTP and HTTPS farms, please follow the procedure.
Go to the List of Rulesets in the section “IPDS > WAF > Rulesets” and start all the farms, the status will become in UP green mode.
Now go to the HTTP or HTTPS farm you want to protect and edit, and click in a new tab “IPDS”, here a view will be loaded with a list of all the available rulesets and which ruleset is applied to the farm.
Please Enable the desired protection rules, take into consideration that the order number is important for the OWASP protection system, you can disable certain protection rules, for example, JAVA protection in case you don’t use Java in the backend but the ruleset needs to appear in this list in the order that numbers show, an example of enabling ALL the rules below:

Testing SKUDONET Open Source WAF configuration.
Run the following curl command to check that a the WAF triggers and inform about a possible attack:
curl http://172.16.100.48/index.php?../../bye SKUDONET WAF replied forbidden
And the following log is triggered in /var/log/syslog.
2024-10-23T05:55:57.798762-04:00 skdce7001 pound: ReverseProxy, SKUDONET ModSecurity: Warning. Matched "Operator `Rx' with parameter `(?:^([\d.]+|\[[\da-f:]+\]|[\da-f:]+)(:[\d]+)?$)' against variable `REQUEST_HEADERS:Host' (Value: `172.16.100.48' ) [file "/usr/local/skudonet/config/ipds/waf/sets/REQUEST-920-PROTOCOL-ENFORCEMENT.conf"] [line "781"] [id "920350"] [rev ""] [msg "Host header is a numeric IP address"] [data "172.16.100.48"] [severity "4"] [ver "OWASP_CRS/4.8.0-dev"] [maturity "0"] [accuracy "0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-protocol"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "capec/1000/210/272"] [tag "PCI/6.5.10"] [hostname "172.16.100.48"] [uri "/index.php"] [unique_id "172967735772.097569"] [ref "o0,13o0,13v40,13"]
2024-10-23T05:55:57.799586-04:00 skdce7001 pound: ReverseProxy, SKUDONET ModSecurity: Warning. Matched "Operator `Rx' with parameter `(?i)(?:[/\x5c]|%(?:2(?:f|5(?:2f|5c|c(?:1%259c|0%25af))|%46)|5c|c(?:0%(?:[2aq]f|5c|9v)|1%(?:[19p]c|8s|af))|(?:bg%q|(?:e|f(?:8%8)?0%8)0%80%a)f|u(?:221[56]|EFC8|F025|002f)|%3(?:2(?:%(?:%6|4)6|F)|5%%63)|1 (394 characters omitted)' against variable `REQUEST_URI_RAW' (Value: `/index.php?../../bye' ) [file "/usr/local/skudonet/config/ipds/waf/sets/REQUEST-930-APPLICATION-ATTACK-LFI.conf"] [line "44"] [id "930100"] [rev ""] [msg "Path Traversal Attack (/../) or (/.../)"] [data "Matched Data: /../ found within REQUEST_URI_RAW: /index.php?../../bye"] [severity "2"] [ver "OWASP_CRS/4.8.0-dev"] [maturity "0"] [accuracy "0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-lfi"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "capec/1000/255/153/126"] [hostname "172.16.100.48"] [uri "/index.php"] [unique_id "172967735772.097569"] [ref "o13,4v4,20"]
2024-10-23T05:55:57.799845-04:00 skdce7001 pound: ReverseProxy, SKUDONET ModSecurity: Warning. Matched "Operator `Rx' with parameter `(?:(?:^|[\x5c/;])\.{2,3}[\x5c/;]|[\x5c/;]\.{2,3}(?:[\x5c/;]|$))' against variable `REQUEST_URI' (Value: `/index.php?../../bye' ) [file "/usr/local/skudonet/config/ipds/waf/sets/REQUEST-930-APPLICATION-ATTACK-LFI.conf"] [line "76"] [id "930110"] [rev ""] [msg "Path Traversal Attack (/../) or (/.../)"] [data "Matched Data: /../ found within REQUEST_URI: /index.php?../../bye"] [severity "2"] [ver "OWASP_CRS/4.8.0-dev"] [maturity "0"] [accuracy "0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-lfi"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "capec/1000/255/153/126"] [hostname "172.16.100.48"] [uri "/index.php"] [unique_id "172967735772.097569"] [ref "o13,4v4,20"]
2024-10-23T05:55:57.800619-04:00 skdce7001 pound: ReverseProxy, [WAF,service Backend, backend 172.16.100.254:80,] (7fbb9423f6c0) [client 192.168.2.21] SKUDONET ModSecurity: Access denied with code 403 (phase 2). Matched "Operator `Ge' with parameter `5' against variable `TX:BLOCKING_INBOUND_ANOMALY_SCORE' (Value: `13' ) [file "/usr/local/skudonet/config/ipds/waf/sets/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "231"] [id "949110"] [rev ""] [msg "Inbound Anomaly Score Exceeded (Total Score: 13)"] [data "client:192.168.2.21"] [severity "0"] [ver "OWASP_CRS/4.8.0-dev"] [maturity "0"] [accuracy "0"] [tag "anomaly-evaluation"] [tag "OWASP_CRS"] [hostname "172.16.100.48"] [uri "/index.php"] [unique_id "172967735772.097569"] [ref ""]
2024-10-23T05:55:57.800796-04:00 skdce7001 pound: ReverseProxy, service Backend, backend 172.16.100.254:80, (7fbb9423f6c0) WAF denied a request from 192.168.2.21
OWASP uses 4 different levels of security, called Paranoia Levels, by default this Paranoia level is configured in 1. if you want to increase this paranoia level please refer to Rule 901120 in file REQUEST-901-INITIALIZATION.
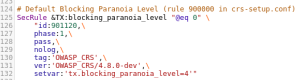
Each save action taken in any Rule will be effective automatically without any farm restart.

