Distributed Denial-of-Service (DDoS) attacks have emerged as a significant threat, posing a serious risk to the stability and accessibility of online services. These threats aim to disrupt the normal functioning of a target system or network by flooding it with a deluge of illegitimate traffic, rendering it overwhelmed and incapable of responding to genuine requests.
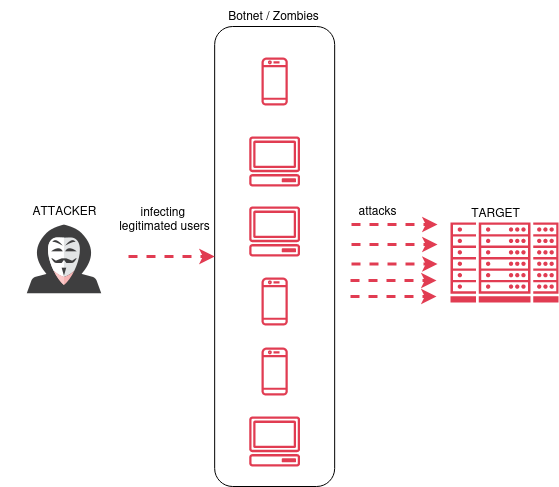
DDoS attacks exploit the interconnected nature of the internet, utilizing a vast network of compromised devices, known as a botnet, to orchestrate the attack. These devices, often unknowingly infected with malware, are remotely controlled by the attacker and instructed to bombard the target with a surge of data requests. This overwhelming influx of traffic consumes the target’s resources, preventing it from serving legitimate users.
DDoS attack visual representation
The consequences of DDoS attacks can be severe, causing financial losses, reputational damage, and even operational paralysis. Businesses heavily reliant on online services are particularly vulnerable to these attacks, as they can lead to interruptions in e-commerce, customer service, and critical business operations.
To mitigate the risk of DDoS attacks, organizations must implement comprehensive cybersecurity measures, including traffic filtering, network monitoring, and DDoS protection services. In this section, we demonstrate how to implement rules to protect against DDoS using SKUDONET ADC.
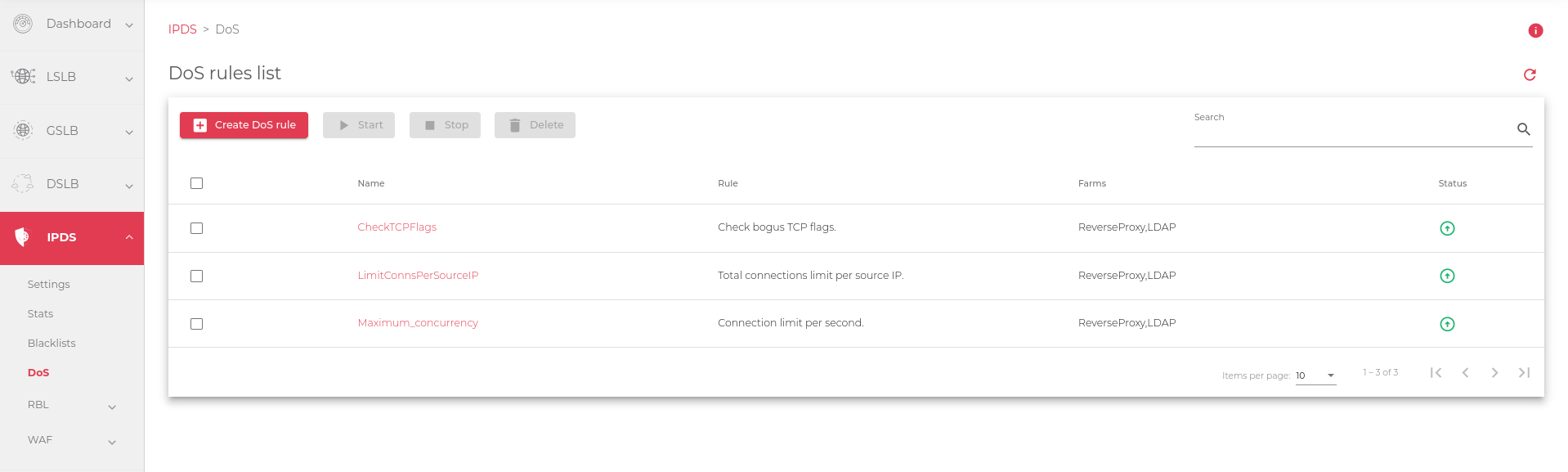
The image below shows a list of DoS rules configured and added to a particular farm:
These are the descriptions of the fields in the image above:
Name: A name that identifies a rule
Rule: The type of DoS rule that will be applied to a farm. These are the preconfigured rules on the ADC.
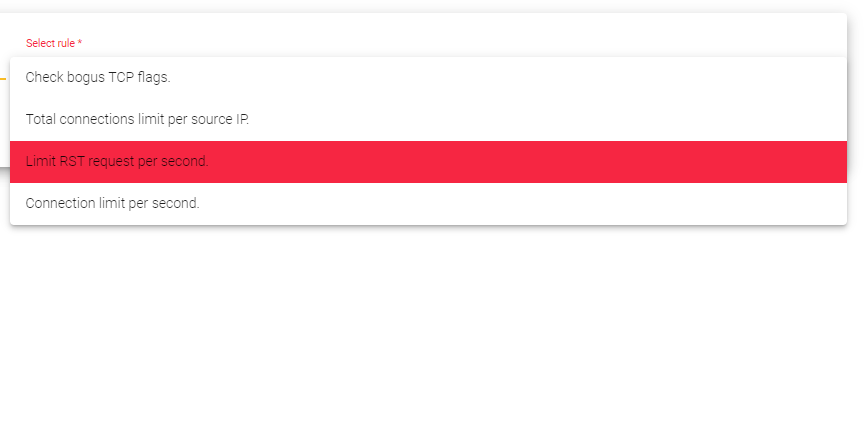
- Check bogus TCP flags: This rule checks for packets with invalid TCP flags. TCP flags are used to control the flow of data between two computers. Packets with invalid TCP flags can be used to exploit vulnerabilities in software and launch denial-of-service attacks.
- Total connections limit per source IP: This rule limits the number of connections from a single source IP address that can access a farm service. This can be used to prevent attackers from using a single IP address to send a large number of requests to a service.
- Limit RST request per second: This rule limits the number of RST requests per second that a farm service will accept. RST (reset) packets are used to terminate TCP connections. An attacker can send a large number of RST packets to a service to disrupt legitimate connections.
- Connection limit per second: This rule limits the number of connections per second that can access a farm service. This is useful for preventing denial-of-service attacks, where an attacker tries to overwhelm a service with so many connections that it becomes unavailable to legitimate users.
Farms: Farms to which the rule is applied
Status: Indicates if the Farm is Enabled or Disabled. A Green circle indicates that it has been enabled, while a Red circle indicates that the rule has been Disabled.
Actions: Allows a user to Create, edit, delete, start, or stop the rule:
- Create DoS rule: Create a new rule to be assigned to certain farm services.
- Edit: Modify the rule’s global settings or assign a farm service if needed.
- Delete: Remove a created farm service rule.
- Start: Activate a system rule.
- Stop: Deactivate a system rule.
Next Article: IPDS | DoS | Create