An RBL(Real-time Blocklist), also known as a DNS-based blocklist (DNSBL), is a spam-fighting tool that maintains lists of IP addresses associated with malicious-related activities. These blocklists method has been used by email servers in the past offering a way of blocking source IPs in user, but SKUDONET offers the possibility of doing the same job but in an early stage of the operating system, in Kernel Space, doing the same task faster so in a better and more efficient way.
SKUDONET offers the RBL filtering possibility of configuration for any farm with any protocol not only for Email servers as in the past, so web traffic, ssh traffic, database traffic or any other kind of traffic can be checked against specific RBL DNS databases.
When the farm wants to check an IP address against an RBL, it will reverse the source IP address and append it to the RBL domain. For example, to check the IP address 192.168.1.100 against the SKUDONET RBL, the email server would query 100.1.168.192.all.skudonet.com
Here are examples of domains maintaining a list of blacklisted IPs.
- all.rbl.skudonet.com
- dnsbl.spamhaus.org
- bl.spamcop.net
- b.xbl.org
- rsbl.mail-abuse.org
- pbl.spamhaus.org
If the IP address is listed on the RBL, the remote RBL system will return a positive response. This tells the SKUDONET IPDS that the IP address is known to be a malicious source, and it will block the message.
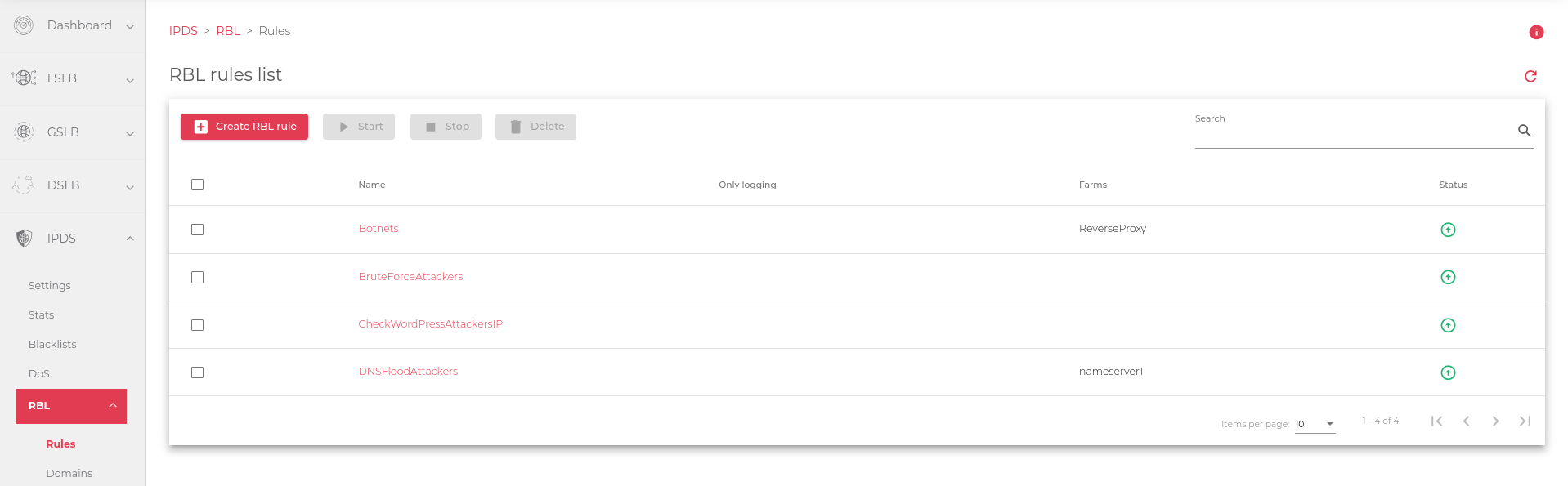
The image below shows a list of configured RBL rules that you can use to protect your farms using RBL checking.
The RBL rules list includes the following fields:
- Name: A unique name for the rule.
- Only Logging: When enabled, the rule does not block any traffic, but it does write logs to the syslog server.
- Farms: A list of farms to which the rule is applied.
- Status: Indicates whether the rule is Enabled or Disabled.
 Green for Enabled,
Green for Enabled,  Red for Disabled
Red for Disabled - Actions: Allows you to edit, start/stop, or delete the rule.