ZSS (VPN Site-to-Site)
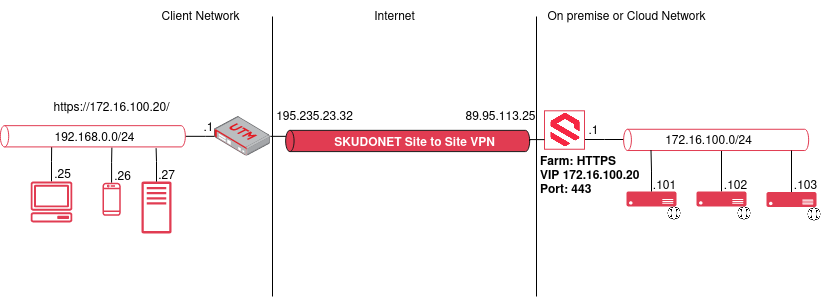
The following diagram describes the use case where VPN Site to Site can be used. The site to Site VPN can be configured to communicate with two different remote networks. From a load balancer perspective to reach the backends or in definitive to communicate any network from/to SKUDONET. The other VPN endpoint needs to support IPsec.
- The client network is a private network in 192.168.0.0/24 with a Gateway 192.168.0.1 on the Router, this router has a Public IP 195.235.223.32 with IPsec support.
- On the other endpoint is SKUDONET with a public IP 89.95.113.25 or any other networking device that forwards the IPsec Traffic to the local SKUDONET IP, but following our example, SKUDONET is directly exposed to the internet on 89.95.113.25 and local IP 172.16.100.1.
- Behind SKUDONET the backends network 172.16.100.0/24 with 3 different backends 172.16.100.101, 172.16.100.102 and 172.16.100.103.
- SKUDONET is configured with a Load Balancing Farm in HTTPS mode with virtual IP 172.16.100.20 and virtual port 443, this farm is configured with a service with the 3 backends previously mentioned. The configuration of the HTTPS profile for this load balancing is out of this article.
- SKUDONET VPN module generates a Site to Site VPN between 89.95.113.25 (Local Endpoint) and 195.235.23.32 (Remote Endpoint)
- clients in network 192.168.0.0/24 connect to SKUDONET VIP load balanced with the URL https://172.16.100.20/ and the Site to Site VPN Configuration makes possible the routing between both networks.
Following this scenario, the configuration of the SKUDONET VPN endpoint should be done as follows:
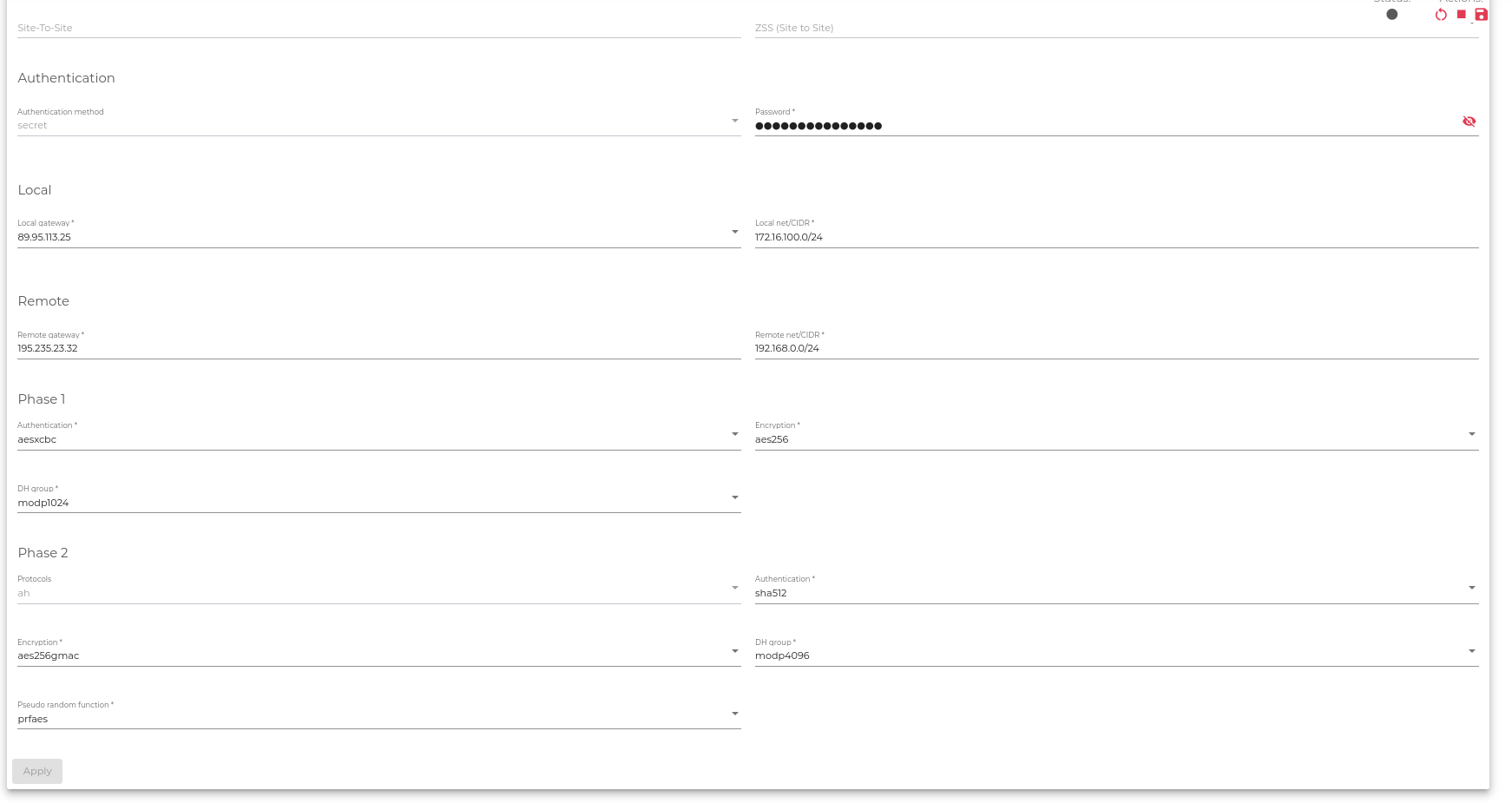
Here is a brief description of the fields you’ll fill in the form.
Authentication
Configure the VPN Authentication method.
Authentication method. The method used to verify submitted credentials. This method is usually kept a secret.
Password. Your user password for accessing the VPN.
Local
Configure the VPN Local Endpoint
Local: Local VPN Endpoint, where the VPN service is listening.
Local net/CIDR: Local Network where VPN traffic is routed.
Remote
Configure the VPN Remote Endpoint
Remote: Remote VPN Endpoint, where the VPN service is listening.
Remote net/CIDR: Remote Network where VPN traffic is routed.
Phase 1
Configure the VPN Phase 1 for crypto security configuration if required.
Authentication: IKE Phase 1 negotiation algorithm that checks the integrity of a request.
Encryption: Encryption algorithms used for securing data packets against packet sniffing.
DH group: An algorithm that provides secrecy of data shared between two unprotected VPN endpoints.
Phase 2
Configure the VPN Phase 2 for crypto security configuration if required.
Protocols: The type of IPsec protocol to be used for authenticating the packets shared over a network.
Authentication: IKE Phase 2 negotiation algorithm that checks the integrity of a request.
Encryption: Encryption methods are used for securing data packets traversing over a network.
DH group: An algorithm that provides secrecy of data shared between two unprotected VPN endpoints.
Pseudo random function: An algorithm that creates randomness, solely for keying purposes.