The SKUDONET Web Application Firewall (WAF) is a tool that can be used to detect and block malicious HTTP traffic. It works by searching and analyzing patterns to apply advanced security policies. These rules are grouped into sets and can be applied to HTTP farms. For HTTPS traffic, WAF rules will be checked after the TLS Encryption has been terminated.
SKUDONET IPDS packages use the OWASP ModSecurity rules, but you can also create your own ruleset to protect your system against any kind of attack. If you want to read more about OWASP rules, refer to the Owasp Modesecurity Project.
By default, the OWASP ruleset uses a scoring system called paranoia levels, and the default level is 1. If you want to read more about these levels, refer to this article: Paranoia levels
If you want to increase the paranoia level, do the following:
- Go to the REQUEST-901-INITIALIZATION ruleset.
- Click the Rules tab.
- Locate the rule number 901120 and edit it in Raw mode
- Change setvar:’tx.blocking_paranoia_level=1′ to the desired paranoia level.
The image below shows a list of preconfigured WAF rules:
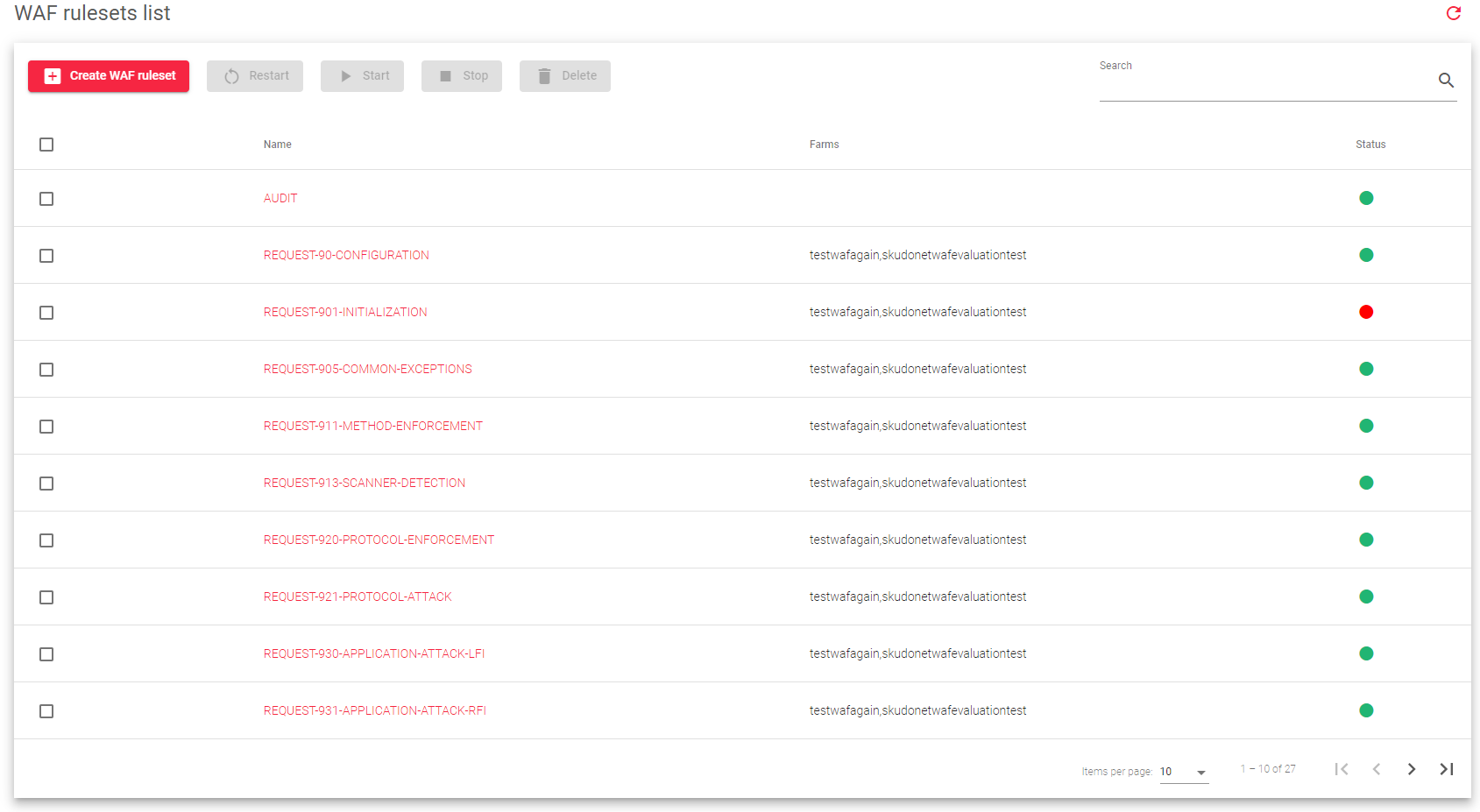
Below are the descriptions for each field in the table shown in the image above.
Name: A unique name for the ruleset.
Farms: The farms to which the ruleset is applied.
STATUS: The ruleset status is represented by the following color codes:
- Green: Enabled. The ruleset is being checked for the farms that are using it.
- Red: Disabled. The ruleset is not enabled, so it is not having any effect on the farm.
Actions: The following actions are allowed for the status of the WAF rules:
- Create WAF ruleset: Opens a form to create a new WAF ruleset.
- Edit: Modify the ruleset settings or assign a farm service, if needed.
- Restart: Reinitialize a WAF rule.
- Start: Apply the WAF ruleset.
- Delete: Remove a ruleset.
Next Article: IPDS | WAF | Rulesets | Create

