Contents
WAF Global Settings
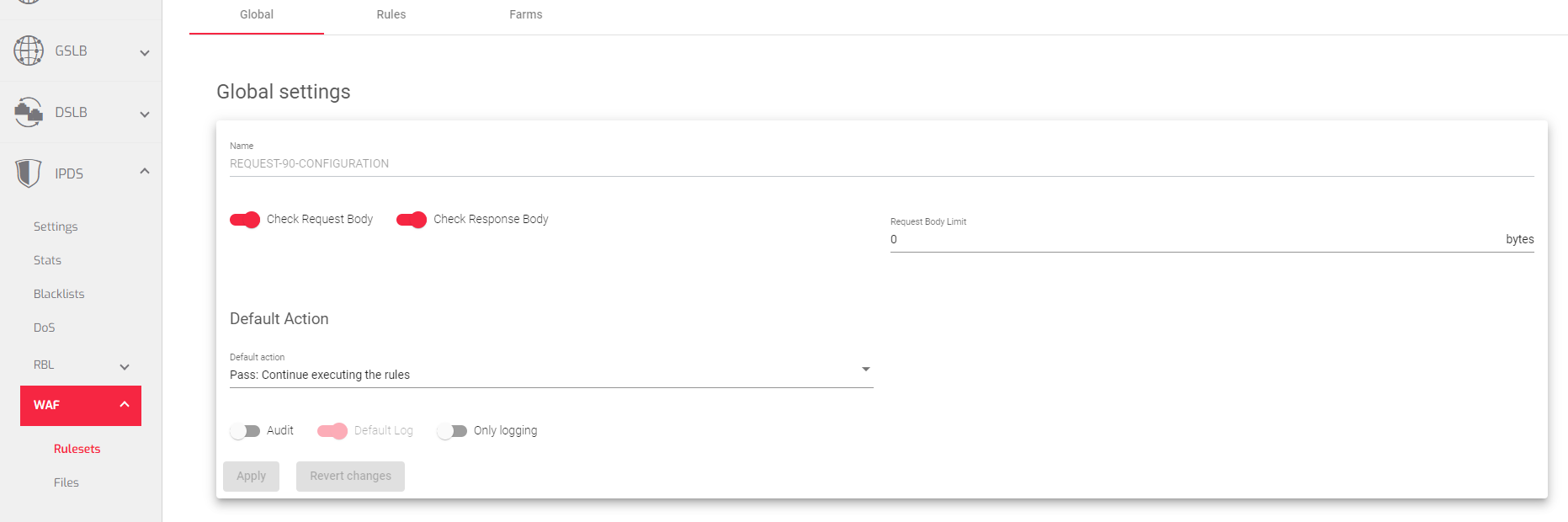
The Global Settings WAF Rule Set section allows you to configure the behavior of all rules contained in the set. You can set the name of the rule set, whether or not to check the request and response bodies, the maximum number of bytes of the request body to save, the default action to take when no resolution is specified in a rule, the default phase to execute the rule in, and the default log action.
Here is a brief description of each setting:
Name: A unique identifier for the rule. This cannot be changed after the rule is created.
Check Request Body: Determines whether the body of HTTP requests should be analyzed. If this option is disabled, the body is not examined, and the WAF does not check the request body parameters.
Request Body Limit: Specifies the maximum number of bytes of the request body that will be saved for inspection. If set to 0, the WAF saves the entire content-length value.
Check Response Body: Determines whether the body of HTTP responses should be analyzed. If this option is disabled, the body is not examined, and the WAF does not check the response body parameters. Responses larger than 524,288 bytes (512 KB) are ignored.
Default Action: These rules apply by default. Here is a summary of each action:
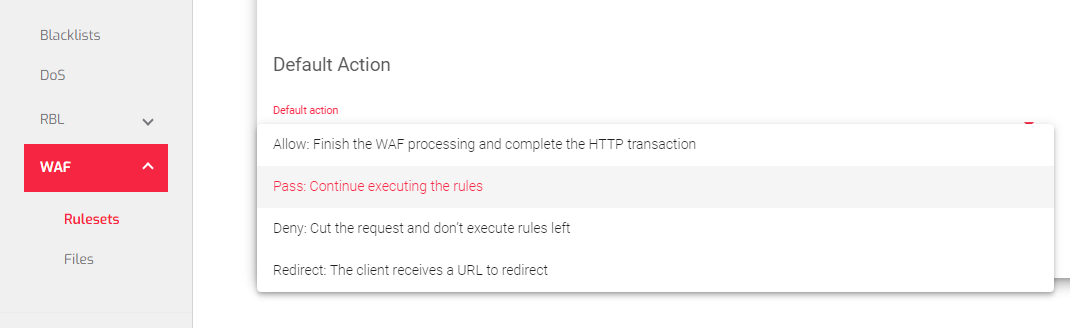
- Allow: Will enable processing of the current WAF till it finishes to complete the HTTP transaction.
- Pass: WAF will continue evaluating the next rule without cutting the HTTP transaction.
- Deny: Finish the current HTTP transaction. Evaluation of more rules will not be allowed. If the rule matches in phase 1 or 2 (analyzing the request), the request will not be delivered to the backend. If the rule matches in phase 3 or 4 (analyzing the response), the response will not be delivered to the client.
- Redirect: The HTTP transaction will be halted and an HTTP redirect will be sent to the client.
Redirect URL: The URL that is sent to the client when a rule matches. This URL has a predetermined redirect resolution.
Default Log: A default logging action. This value is used if no specific logging action is specified in the rule settings.
Only Logging: When this option is enabled, the resolution parameter of the rules in the set will never be executed. This mode is only available when the set is running.
Rules
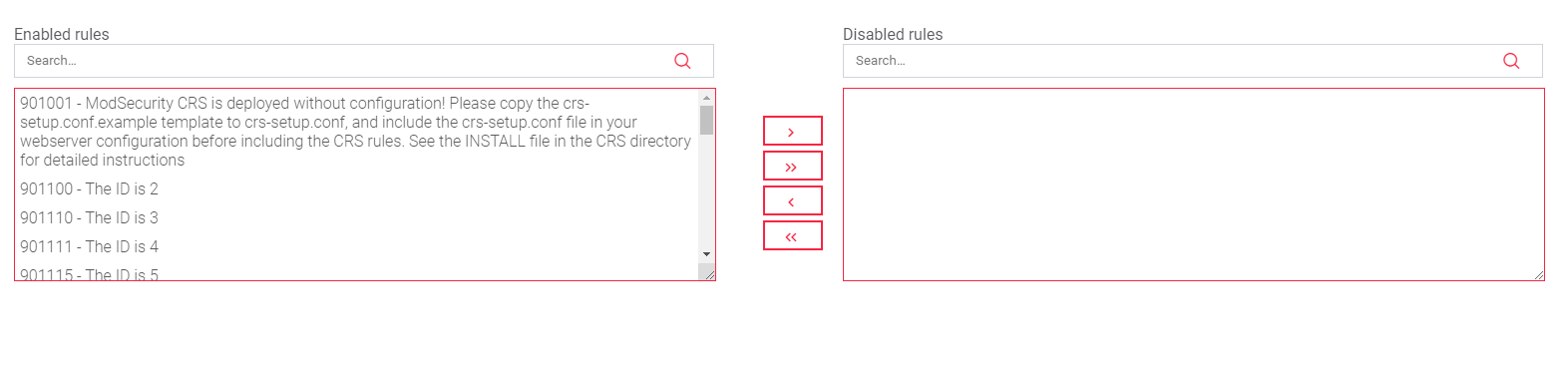
The image above shows two tables, one for Enabled rules and the other for Disabled rules.
- Enabled Rules: This is a list of all the rules that are currently enabled in the set. Each rule is identified by its rule ID and description parameters.
- Disabled Rules: This is a list of all the rules that are currently disabled in the set.
List of WAF Rules
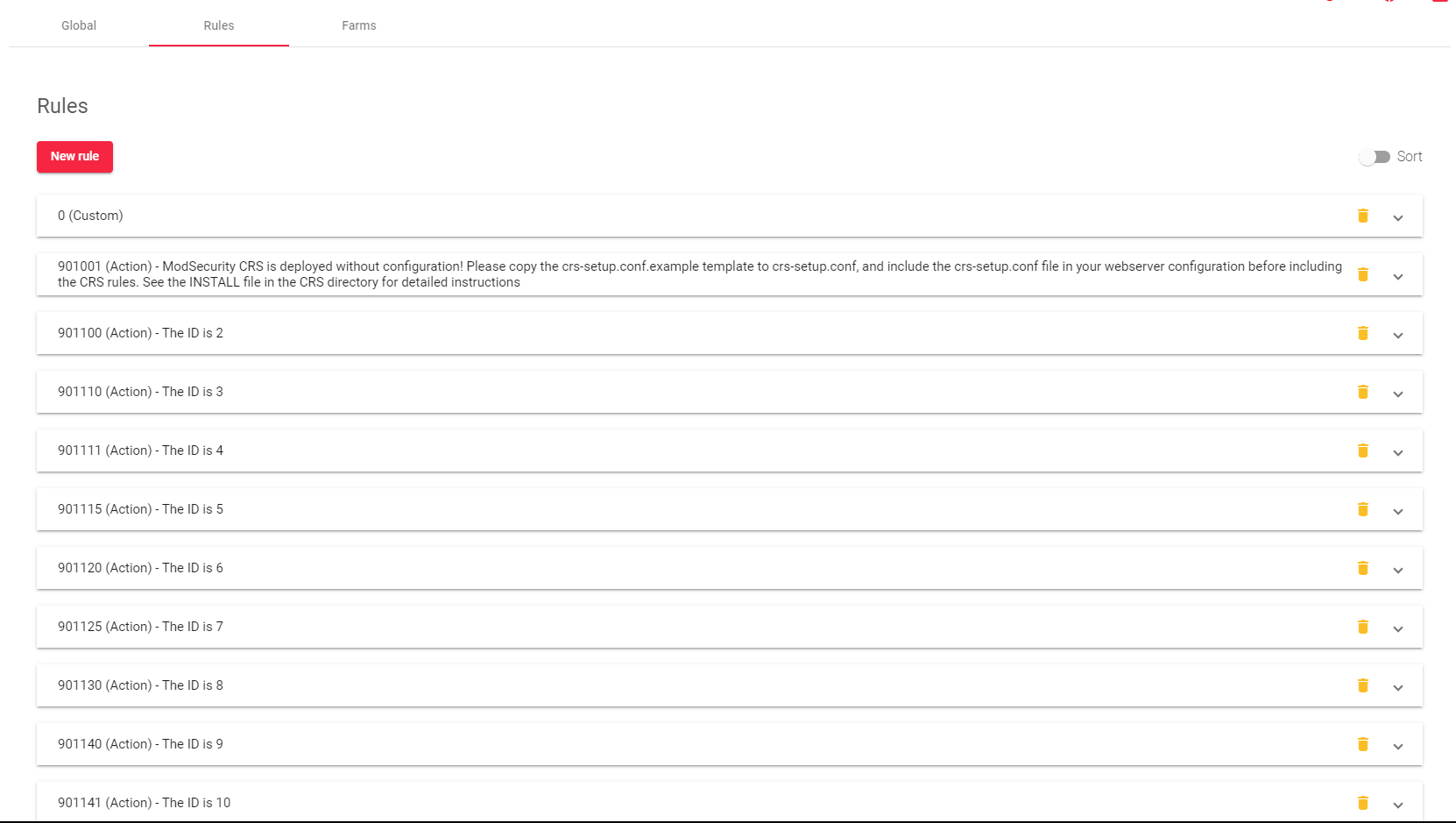
The WAF Rules section allows you to create and manage WAF rules that can detect and protect against HTTP attacks.
These rules are directives that are evaluated sequentially, in the order that they are displayed on the screen.
You can Sort the rules by dragging and dropping them into the desired order.
Each rule has the following parameters:
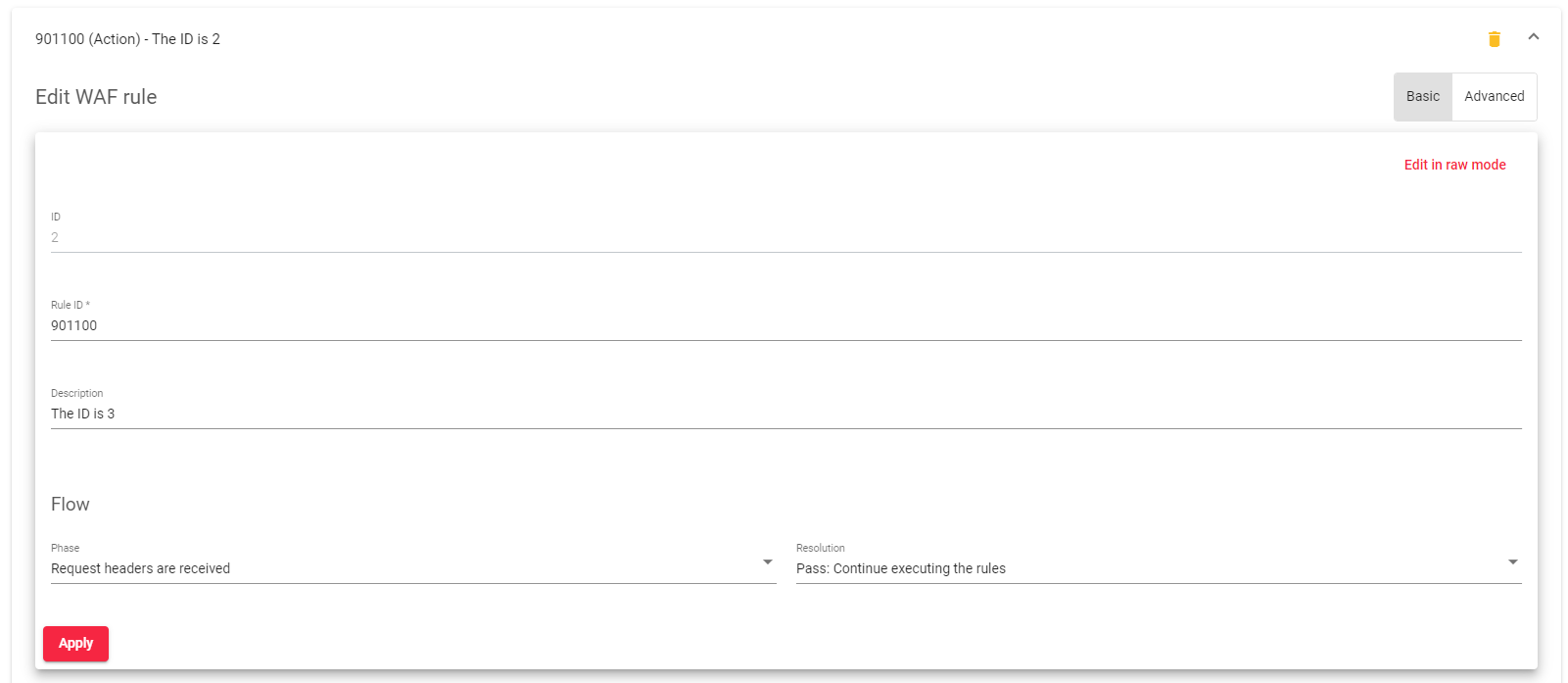
ID: A unique identifier for the rule within the rule set.
Rule ID: A unique identifier for the rule. Two rules in the same rule set cannot have the same rule ID.
Description: A descriptive message for the rule. This message will be logged if the rule matches a request.
Phase: The step of the HTTP request where the rule will be executed. The possible phases are:
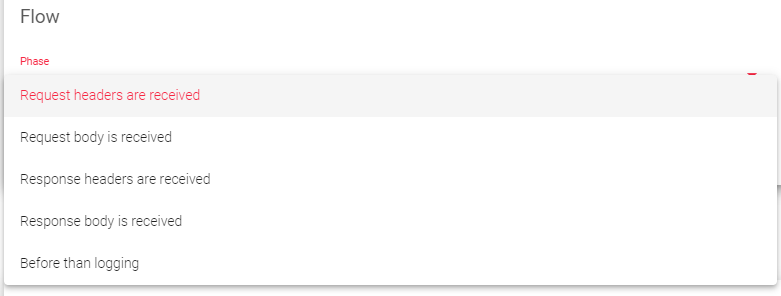
- Request headers are received: The rule will be executed after all request headers from the client have been read by the load balancer.
- Request body is received: The rule will be executed after the complete request body from the client has been buffered in the load balancer.
- Response headers are received: The rule will be executed after all response headers from the server have been read by the load balancer.
- Response body is received: The rule will be executed after the complete response body from the server has been read by the load balancer.
- Before than logging: The rule will be executed after the WAF process has finished logging.
Resolution: The action to take if all of the match conditions are met. The possible resolutions are:
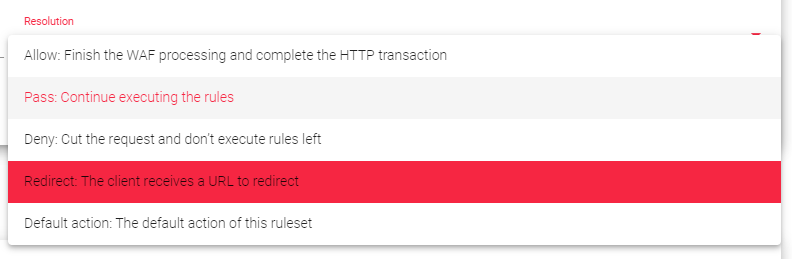
- Allow: No more rules will be evaluated for the current HTTP transaction.
- Pass: WAF will continue evaluating the next rule without interrupting the HTTP transaction.
- Deny: The current HTTP transaction will be terminated. No more rules will be evaluated.
- Redirect: The HTTP transaction will be halted and the client will be redirected to a new URL.
- Default Action: If no resolution is specified, the default action will be used. This is usually the Allow resolution.
Advanced WAF settings
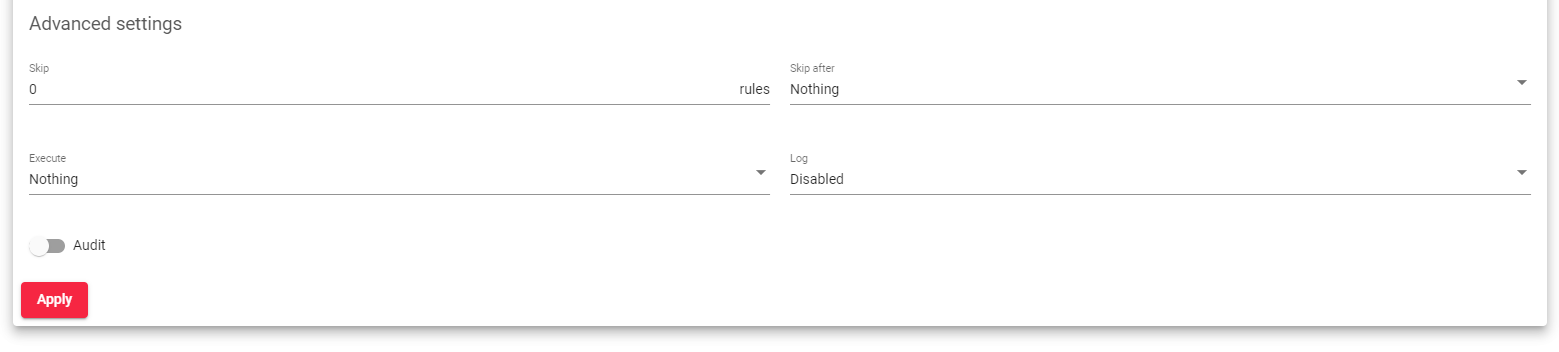
Skip: If all of the match conditions are met, the rule will skip the specified number of other rules.
Skip After: If all of the match conditions are met, the rule will jump to another position in the firewall. The rule can jump to a ‘mark’ or to another rule ID. The rule ID will be executed after the jump and will be in the same phase as the current rule.
Execute: The path to a LUA script. The script must be uploaded to the load balancer before it can be used. The script will be executed if the first match is achieved.
Log: If this parameter is enabled, the rule will be logged when the first match is achieved.
Editing a WAF in Raw Mode
If the form mode is not enough to describe a WAF rule, and the administrator is familiar with the SecLang syntax, they can create rules or a batch of rules in raw mode. This mode accepts any instructions, including instructions and parameters that are not supported by the form mode. These unsupported parameters will not be shown in the form mode, but they will be shown in the raw mode and processed when the rule is executed.
Here is an example of the difference between form mode and raw mode:
Form mode:
SecRule REQUEST_METHOD "^POST$"
"id:'1001', phase:1, action:'deny'"
This rule matches all POST requests and denies them.
Raw mode:
SecRule REQUEST_METHOD "^POST$"
"id:'1001', phase:1, action:'deny',
log:'yes', block:'yes'"
This rule matches all POST requests, denies them, logs them, and blocks them. The log: and block: parameters are not supported by the form mode, but they can be used in raw mode.
Raw mode is more powerful than form mode, but it is also more difficult to use. It is important to understand the SecLang syntax before using raw mode to edit WAF rules.
List Of Conditions
The image below shows the conditions that the parsed HTTP packet must match in order for the rule to be applied.
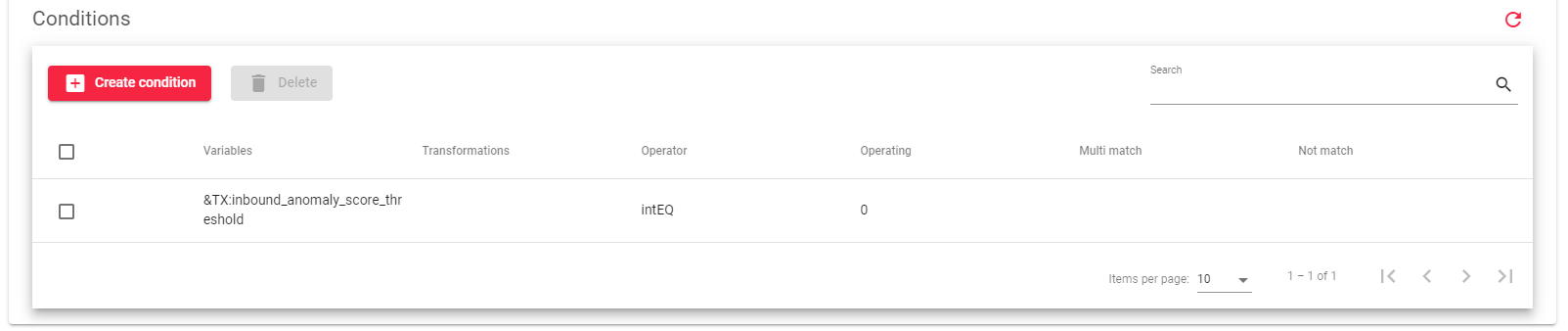
All of these matches will be executed in the phase defined in the rule. The matches will be checked sequentially and the rule will be applied if all of them are successful.
To evaluate the match, the WAF will perform an operation (specified by the Operator and Operand parameters) on a list of variables. If any of the variables in the list meet the condition, then the match is considered successful.
First, the WAF decodes each header in base64 and then converts it to lowercase. Once the variables have been transformed, the WAF applies a regular expression to the list of transformed variables, looking for the string images. The multi-match option will try to match each transformation (after base64 decoding and after lowercase conversion).
Creating Conditions
To create a condition:
- Click the Create condition button.
- Select a variable of a list of them from the variables field. Optionally toggle on the Count elements of variables button if you want to track the count.
- From the Transformation field, select any of the available options. We’ll discuss more about transformations in the next section.
- Select the Operator for your rule. We’ll also discuss more about these in the next section.
- Enter the value to be matched in the Operating section.
- Click the Apply button.
The following are the configuration parameters for setting conditions:
Variable: The part of the HTTP transaction that the rule will match. Read more about Variables in the Creating Variables section below.
Transformations: A list of modifications that are applied to the variables before they are evaluated by the condition. Transformations are applied sequentially, and the multi-match option can be used to try a match for each transformation. Valid transformations include:
- BASE64DECODE: Decodes the variable from base64.
- TOLOWERCASE: Converts the variable to lowercase.
- TRIM: Removes whitespace from the beginning and end of the variable.
- URLDECODE: Decodes the variable from URL encoding.
Operator: The operation that is performed on the variables. Valid operators include:
- CONTAINS: Checks if the variable contains the operand.
- EQUALS: Checks if the variable is equal to the operand.
- GREATER_THAN: Checks if the variable is greater than the operand.
- GREATER_THAN_OR_EQUAL: Checks if the variable is greater than or equal to the operand.
- LESS_THAN: Checks if the variable is less than the operand.
- LESS_THAN_OR_EQUAL: Checks if the variable is less than or equal to the operand.
- MATCHES: Checks if the variable matches the regular expression specified in the operand.
Operand: The value that is compared to the variables. The type of the operand must match the type of the variables.
Multi-Match: If this parameter is enabled, the WAF will try a match for each transformation that is applied to the variables.
Not Match: If this check-box is enabled, the result of the match will be negated.
Creating Variables
Variables are required parameters for match conditions. They specify the part of the HTTP request or response that will be searched for the information.
- Variable: This parameter specifies the field of the HTTP request or response to search for the information (e.g., time, server).
- Variable’s argument: When a variable is selected, it may be necessary to specify an element from it. For example, in the image below, the request header host is selected.
- Count elements of variables: This checkbox counts the number of elements in the variable. This feature is useful when the variable is a list.
Table of Variables.
| Variable | Description |
|---|---|
| ARGS | A collection of the values of arguments in a request. |
| ARGS_JSON | A collection of the values of arguments in a JSON request. This variable is only available if the WAF is configured to parse JSON arguments. The rule set REQUEST-901-INITIALIZATION must be enabled to use this variable. |
| ARGS_COMBINED_SIZE | The total size of the request parameters, excluding files. |
| ARGS_NAMES | A collection of the names of the arguments in a request. |
| FILES | The file names in the user file system. This variable is only available if the request data is multipart/form-data. |
| FILES_COMBINED_SIZE | The total size of the files in a request. This variable is only available if the request data is multipart/form-data. |
| FILES_NAMES | A list of file names used to upload the files. This variable is only available if the request data is multipart/form-data. |
| FILES_SIZES | A list of individual file sizes. This variable is only available if the request data is multipart/form-data. |
| REQBODY_ERROR | A variable that is set to 1 if the request body format is not correct for JSON or XML, and 0 otherwise. |
| REQUEST_BODY | The raw body of the request. If the request does not have the “application/x-www-form-urlencoded” header, you must use “ctl:forceRequestBodyVariable” in the REQUEST_HEADER phase. |
| REQUEST_BODY_LENGTH | The number of bytes in the request body. |
| REQUEST_COOKIES | A list of all request cookie values. |
| REQUEST_COOKIES_NAMES | A list of all request cookie names. |
| REQUEST_HEADERS | All request headers. |
| REQUEST_HEADERS_NAMES | A list of all request header names. |
| REQUEST_METHOD | The request method (e.g., GET, POST, PUT, DELETE). |
| REQUEST_PROTOCOL | The request HTTP version protocol (e.g., HTTP/1.1, HTTP/2). |
| REQUEST_URI | The URI request path, excluding the virtual host. |
| PATH_INFO | The information before the URI path. |
| FULL_REQUEST | The full request. |
| FULL_REQUEST_LENGTH | The number of bytes in the full request. |
| RESPONSE_BODY | The raw body of the response. |
| RESPONSE_CONTENT_LENGTH | The number of bytes in the response body. |
| RESPONSE_HEADERS | All response headers. |
| RESPONSE_HEADERS_NAMES | A list of all response header names. |
| RESPONSE_PROTOCOL | The response HTTP version protocol (e.g., HTTP/1.1, HTTP/2). |
| RESPONSE_STATUS | The response HTTP code (e.g., 200, 404, 500). |
| REMOTE_ADDR | The IP address of the client. |
| REMOTE_PORT | The port where the client initiated the connection. |
| REMOTE_USER | The name of the authenticated user. |
| TIME | The server time in the format hours:minutes:seconds. |
| DURATION | The number of milliseconds since the start of the current transaction. |
| MULTIPART_FILENAME | The filename field in a multipart request. |
| MULTIPART_NAME | The name field in a multipart request. |
| MATCHED_VAR | The matched value in the last match operation. This value does not need the capture option but it is replaced in each match operation. |
| MATCHED_VARS | A list of all matched values. |
| SERVER_ADDR | The IP address of the server. |
| SERVER_NAME | The virtual host that was obtained from the request URI. |
| ENV | The environment variables of the WAF. |
| TX | A collection of variables for the current transaction. These variables are removed when the transaction ends. The variables TX:0-TX:9 store the values captured with the strRegex or phrases operators. |
Table of Operators
WAF operators can have different contexts, which are indicated by prefixes such as int for integer operations, IP for IP operations, str for string operations, and validate for data validation.
Validates variables that are UTF-8. This operator does not expect any operating.
| Operator | Description |
|---|---|
| strBegins | Matches if any of the variables begin with the value of operating. |
| strContains | Matches if any of the variables contain the value of operating. |
| strContainsWord | Matches if any of the variables contain the word or the value of the operating. |
| strEnd | Matches if any of the variables end with the value of operating. |
| strWithin | Matches if any of the variables start with the value of operating. |
| strMatch | Matches if any of the variables match the value of operating. This operating can be a list of strings split by the character |
| strEq | Matches if any of the variables is identical to the value of the operating. |
| strRegex | Matches if any of the variables match the regular expression used in operating. |
| strPhrases | Matches if any of the variables match any of the values of the list operating. |
| strPhrasesFromFile | Matches if any of the variables match any of the values of the list in the file specified by operating. |
| intEQ | Matches if any of the variables is equal to the number used in operating. |
| intGE | Matches if any of the variables is greater or equal to the number used in operating. |
| intGT | Matches if any of the variables is greater than the number used in operating. |
| intLE | Matches if any of the variables is lower or equal to the number used in operating. |
| intLT | Matches if any of the variables is lower than the number used in operating. |
| detectSQLi | Detects an SQL injection on the list of variables. This operator does not expect any operating. |
| detectXSS | Applies the detection of XSS injection to the list of variables. This operator does not expect any operating. |
| ipMatch | Attempts matching the IP or network segments of operating with the list of variables. |
| ipMatchFromFile | Matches the IP or network segments of operating with the list of IPs and network segments in the file specified by operating. |
| validateByteRange | Ensures that the number of bytes of the variables is in one of the operating values. An example of operating is “10, 13, 32-126”. |
| validateUrlEncoding | Validates encoded data. This operator must be used only for data that does not encode data commonly or for data that are encoded several times. |
| validateUtf8Encoding | |
| verifyCreditCard | Verifies if variables are credit card numbers. This parameter accepts a regular expression as operating. If it matches, then it will successfully verify the card. |
| verifySSN | Verifies if variables are a US Social Security Number. This parameter accepts a regular expression as operating, if it matches then it applies the SSN verify. |
| matchAllways | Always returns true, forcing a match. |
| matchNever | Always returns false, forcing a non-match. |
Table of Transformation
| Transformation | Description |
|---|---|
| base64Decode | Convert Base64-encoded string to original form. |
| base64DecodeExt | Convert Base64-encoded string to original form, ignoring invalid characters. |
| sqlHexDecode | Convert SQL hex data to original form. |
| base64Encode | Convert string to Base64-encoded form. |
| cmdLine | Avoid problems with escaped command line. |
| compressWhitespace | Convert whitespace characters to spaces, merging multiple consecutive spaces into one. |
| cssDecode | Decode characters encoded using CSS 2.x escape rules. |
| escapeSeqDecode | Decode ANSI C escape sequences, leaving invalid encodings unchanged. |
| hexDecode | Decode string encoded using the same algorithm as hexEncode. |
| hexEncode | Convert string to hexadecimal-encoded form. |
| htmlEntityDecode | Decode HTML entities. |
| jsDecode | Decode JavaScript escape sequences. |
| length | Return length of input string in bytes, as a string. |
| lowercase | Convert all characters to lowercase using the current C locale. |
| md5 | Calculate MD5 hash of input string. |
| none | Remove previous transformation functions associated with the current rule. |
| normalizePath | Remove multiple slashes, directory self-references, and directory back-references from the input string, except when at the beginning of the input. |
| normalizePathWin | Same as normalizePath, but first convert backslash characters to forward slashes. |
| parityEven7bit | Calculate even parity of 7-bit data. |
| parityOdd7bit | Calculate odd parity of 7-bit data. |
| parityZero7bit | Calculate zero parity of 7-bit data. |
| removeNulls | Remove all NUL bytes from input. |
| removeWhitespace | Remove all whitespace characters from input. |
| replaceComments | Replace C-style comments with a single space, merging multiple consecutive occurrences of space. |
| removeCommentsChar | Remove common comments chars. |
| replaceNulls | Replace NUL bytes in input with space characters. |
| urlDecode | Decode URL-encoded input string, ignoring invalid encodings. |
| uppercase | Convert all characters to uppercase using the current C locale. |
| urlDecodeUni | Decode URL-encoded input string with support for Microsoft-specific %, u encoding. |
| urlEncode | Encode input string using URL encoding. |
| utf8toUnicode | Convert all UTF-8 characters sequences to Unicode. |
| sha1 | Calculate SHA1 hash of input string. |
| trimLeft | Remove whitespace from the left side of the input string. |
| trimRight | Remove whitespace from the right side of the input string. |
| trim | Remove whitespace from both the left and right sides of the input string. |
Farms
The Farms WAF Settings section allows you to assign the current WAF rule set to one or more HTTP(s) farms.
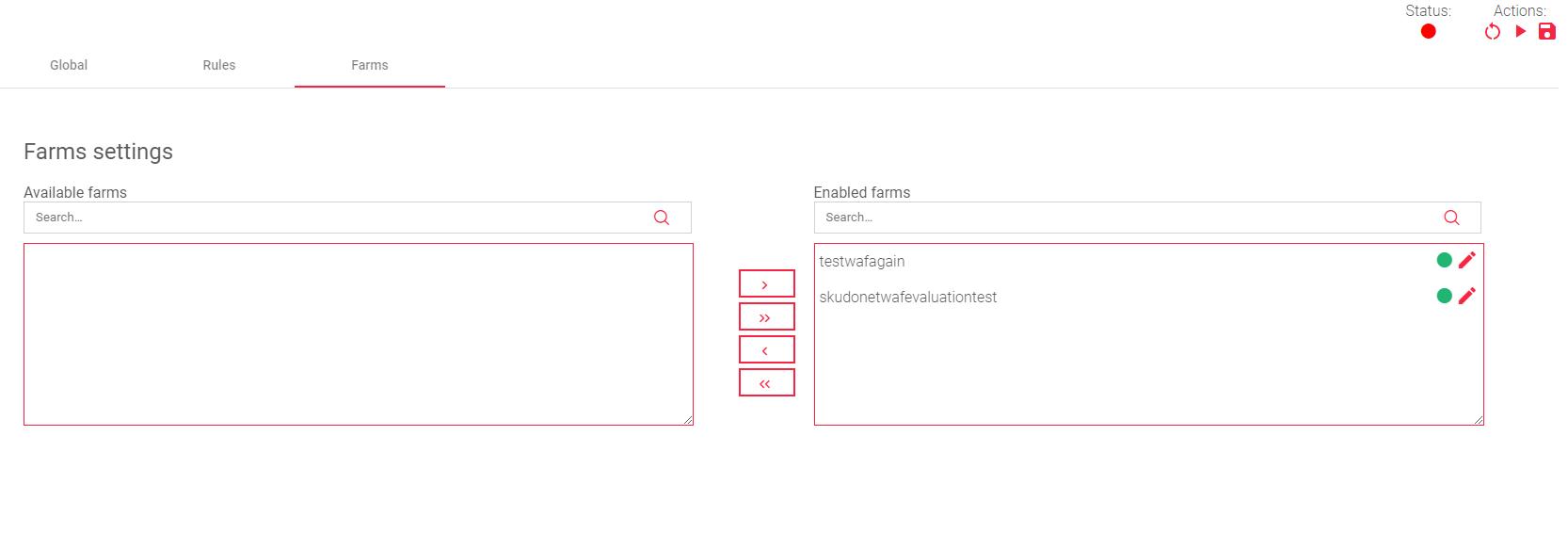
To enable or disable WAF rules on a Farm, Drag and Drop them from the Available farms to the Enabled farm box or viceversa.
Next Article: IPDS | WAF | Files